Resources
Stay up to date on company and partner news, product tips, and industry trends.
-
 How to get started with phishing-resistant MFA to secure federal systems integrators
How to get started with phishing-resistant MFA to secure federal systems integratorsExplore best practices for implementing phishing-resistant multi-factor authentication (MFA) tailored for Federal Systems Integrators (FSIs) to enhance security against sophisticated cyber threats.
Read more -
 What is FIDO and why is it important for business security?
What is FIDO and why is it important for business security?Learn what FIDO is, how it works, and how your organization can benefit from deploying FIDO-based authentication across critical business scenarios.
Read more -
 Securing the world’s critical infrastructure against modern cyber threats
Securing the world’s critical infrastructure against modern cyber threatsLearn how to safeguard IT/OT systems and the supply chain with Zero Trust using phishing-resistant MFA and hardware-backed security.
Read more -
 How to get started with phishing-resistant MFA to secure pharmaceuticals
How to get started with phishing-resistant MFA to secure pharmaceuticalsLearn the six deployment best practices that can help the pharmaceutical industry accelerate adoption of modern, phishing-resistant MFA at scale using the YubiKey.
Read more -
 How to get started with phishing-resistant MFA to secure telecommunications
How to get started with phishing-resistant MFA to secure telecommunicationsLearn deployment best practices to accelerate adoption at scale and secure your organization from account takeovers for telecommunications.
Read more -
 State and local government best practices guide
State and local government best practices guideLearn the six deployment best practices that can help your agency accelerate adoption of modern, phishing-resistant MFA at scale.
Read more -
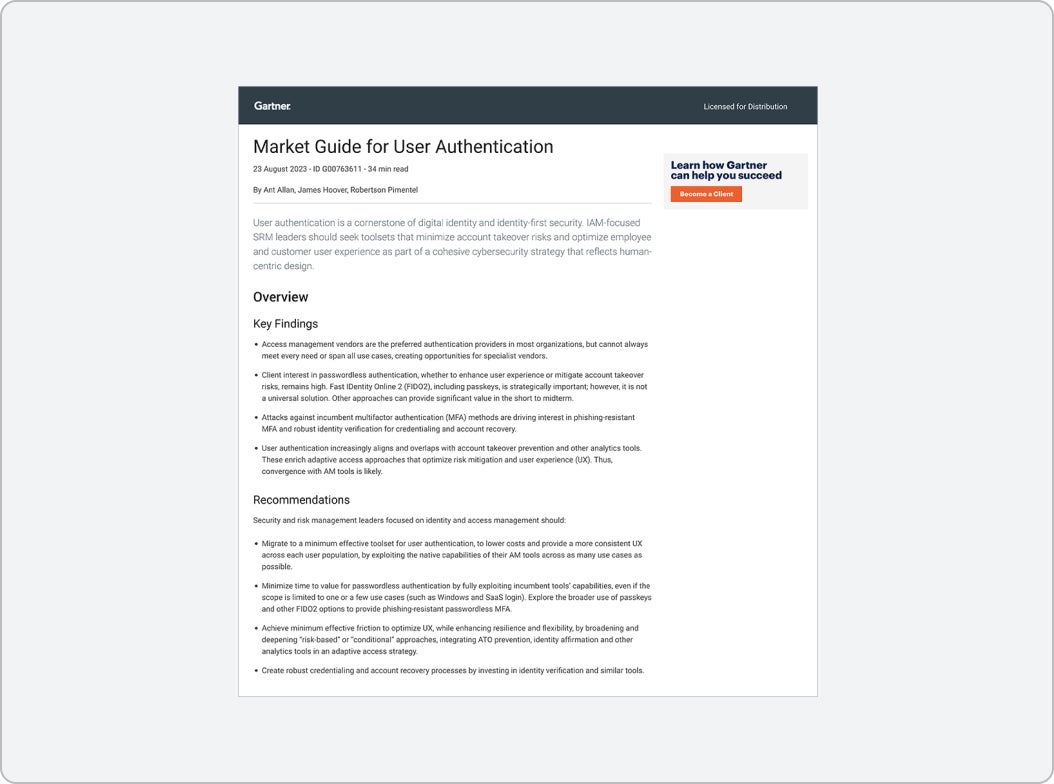 2023 Gartner® Market Guide for User Authentication
2023 Gartner® Market Guide for User AuthenticationDiscover the latest in phishing-resistant multi-factor authentication (MFA) and how to minimize time to value for passwordless authentication, including the use of passkeys. Yubico is a Representative Vendor in the 2023 Gartner® Market Guide for User Authentication.
Read more -
 Building a phishing-resistant enterprise with device-bound passkeys
Building a phishing-resistant enterprise with device-bound passkeysBuilding an enterprise that stops account takeovers with phishing-resistant MFA using a device-bound passkey strategy.
Read more -
 How to get started with phishing-resistant MFA to secure healthcare
How to get started with phishing-resistant MFA to secure healthcareDownload the healthcare best practices guide to learn six deployment best practices to accelerate adoption at scale.
Read more -
 Secure your AWS environment with highest-assurance phishing-resistant MFA
Secure your AWS environment with highest-assurance phishing-resistant MFADownload the best practice guide to learn more how you can stop account takeovers and go passwordless for a wide variety of AWS use cases
Read more
